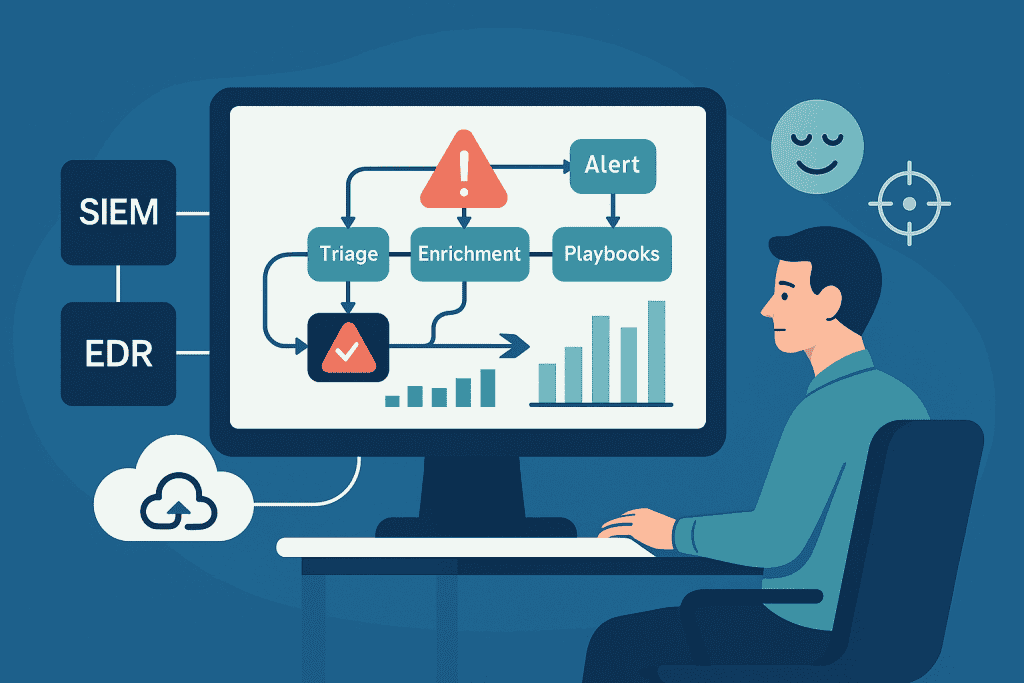
Your security team doesn’t have an alert problem; it has a time problem. They’re busy clearing false positives and piecing together logs from various tools. Meanwhile, real threats slip by because no one sees the full picture in time.
A managed SOAR platform changes that by tying your tools together, automating response playbooks, and surfacing what actually matters. Analysts should stop chasing noise. Instead, they need to focus on real threat hunting and incident strategy.
It’s not another product in the stack, it’s a different way to run your SOC. Keep reading to see what that shift looks like.
Key Takeaways
- Drastically cuts incident response time, reducing threat dwell time from hours to minutes.
- Automates repetitive tasks, freeing analysts to focus on complex investigations and threat hunting.
- Centralizes and orchestrates all security tools, providing a single pane of glass for your entire operation.
It feels like a war of attrition sometimes. The alerts never stop. Each one demands a slice of an analyst’s attention, a manual check across different consoles.
The context needed to understand if an alert is a real threat is scattered everywhere. This is the daily reality for many security teams, and it’s unsustainable.
A managed SOAR platform addresses this fundamental problem. It serves as the brain for your security operations, linking everything automatically. This approach is similar to how an MSSP security service functions by acting as an extension of your security team, ensuring continuous monitoring and expert response.
From Frantic to Focused: The Power of Automation
Imagine this: a security alert pops up in the middle of a busy day. In a traditional SOC, an analyst must stop their work.
They log into four or five tools, run separate searches, and copy data between screens. They try to make sense of it all while time runs out.
They pull threat intel, check the endpoint, and review cloud logs. But by then, they’re already behind on the next alert. With a SOAR platform, that whole messy part shifts into the background [1].
The platform handles the work as soon as the alert is generated, so the analyst can focus on what matters.
It automatically pulls in threat intelligence, checks endpoint status, looks at SIEM and cloud logs, and ties the pieces together into a single, enriched view.
All before a human ever steps in. Automated data enrichment is the first key step. Without context, even a skilled analyst can only guess. With context, they’re making decisions. And sometimes, the platform doesn’t just prepare the data, it acts on it.
For low-fidelity alerts or known-bad indicators, the SOAR can use a set playbook. It’s like a recipe your team decided on beforehand.
If a workstation is clearly compromised, the platform might isolate the endpoint from the network, block a malicious IP address at the firewall, reset user credentials, and open a ticket in your ITSM tool.
Everything happens automatically. There are no dashboards to navigate. Routine cases need no manual approvals.
Depending on organizational policies. This is where you really start to see the impact on Mean Time to Respond (MTTR).
Responses occur in minutes, sometimes just seconds, instead of hours of manual back-and-forth. Palo Alto Networks reports that this type of automation can cut time spent on remediation by up to 90%. source citation or note “according to vendor reports.
That’s not a small improvement, that’s a completely different way of working. It’s about catching an incident early or chasing it after it spreads through the network. But the numbers only tell part of the story.
The deeper benefit of automation is what it does to the human side of the SOC. When a team spends their day closing out repetitive alerts and doing copy‑paste work across tools, it wears them down.
Alert fatigue isn’t just a concept. It causes missed incidents, poor decisions, and tired analysts leaving for other jobs. By letting the platform absorb the constant stream of low‑value alerts, you take a huge weight off the team.
Suddenly, analysts have the space to use their actual expertise. Instead of babysitting noisy alerts, they can focus on what humans are good at: spotting patterns that don’t fit, following hunches, digging into complex incidents, and running proactive threat hunts.
They can check for lateral movement, odd privilege use, or hidden command-and-control traffic. Meanwhile, the platform takes care of the usual “seen this 100 times” situations. Morale improves when people feel like specialists, not button‑clickers.
Here’s how that flow usually looks in practice:
- Automated Triage – The platform ranks alerts based on severity, asset value, user behavior, and custom rules. That means the most dangerous alerts rise to the top instead of getting buried.
- Instant Enrichment –It gathers data from threat feeds, SIEM, EDR, identity systems, and cloud platforms. Then, it attaches everything to the alert in one spot. No tab‑hopping, no repeated queries.
- Pre‑Built Playbooks – These are complex response workflows. They start from one trigger. This trigger can be an alert, an analyst decision, or a scheduled task. You can standardize the “right way” to respond and let the platform enforce it.
Over time, this shift changes the role of the SOC itself. What felt like a constant fight—putting out one fire and seeing five more—now resembles a real command center.
The automation layer handles clear patterns, known malware, obvious phishing, and typical access issues. Your team handles unique situations. You work in gray areas that need judgment and creativity.
That’s the real power of automation in security: not just speed, but focus. The machines take on the grind, and the humans get to do the thinking.
Unifying Your Security Toolset
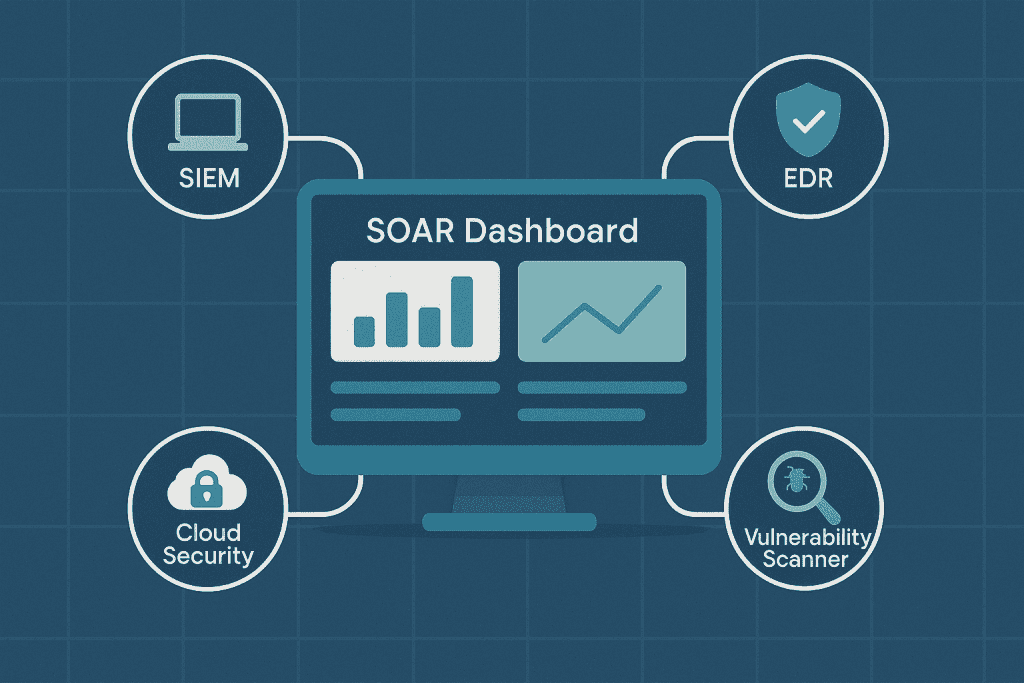
Most organizations have a patchwork of security tools. A SIEM here, an EDR tool there, a cloud security platform, and a vulnerability scanner.
To unify these, the platform orchestrates tools just like an outsourced security operations center that centralizes threat detection and incident handling for businesses without the overhead of in-house teams.
They rarely talk to each other. This creates information silos. Analysts become jacks-of-all-trades but masters of none with tool interfaces.
A managed SOAR platform is like a universal translator for your security team. It helps coordinate their efforts effectively. It integrates with these disparate systems through APIs. This integration is the “orchestration” part of SOAR.
Your CrowdStrike EDR data can automatically connect with alerts from Azure Security Center. The platform spots connections that a person would miss while switching screens.
This unified view appears on a single dashboard. It lets your team see the whole attack surface, from the cloud to the corporate network. This centralization also standardizes processes.
All incidents are managed through the same SOAR platform. This keeps logging and documentation consistent. This is a huge boon for compliance.
Regulations like GDPR and HIPAA require detailed audit trails of security incidents. A managed SOAR platform logs every action by the system or analyst. This creates a complete record for auditors.
It turns a painful, manual process into a simple report generation task. The scalability offered by this model is significant.
As your organization grows, the SOAR platform can integrate new technologies. For managed security service providers (MSSPs), this is particularly powerful.
It streamlines the onboarding of new clients, allowing for a standardized service delivery model that is both efficient and scalable. The platform grows with your needs, without requiring a linear increase in headcount.
Making Data-Driven Security Decisions
Credits: Maven Analytics
Beyond just automation, a mature managed SOAR platform provides analytics. It turns operational data into actionable intelligence.
This data-driven security decision-making reflects the evolving role of how an MSSP works by continuously optimizing security stacks and improving threat hunting effectiveness.
You can see metrics on everything from the volume of alerts by type to the average time to close incidents.
This data helps you answer critical questions. Are we improving? Where are our biggest bottlenecks? Which playbooks are most effective? This visibility allows for continuous improvement of your security posture.
You might discover that a particular type of alert is almost always a false positive. You can then tune the detection rule at the source, reducing noise for everyone.
You might notice that issues with a specific application take longer to fix. This could mean you need a better playbook or extra training. This feedback loop is essential for building a more resilient security program over time.
The platform also helps operationalize threat intelligence. Instead of a weekly report that gets filed away, threat intel feeds can be integrated directly into the SOAR.
When a new indicator of compromise (IOC) is published, the platform can immediately search your environment for matches.
This moves your team to a proactive, intelligence-driven method. Now, you can hunt threats using the latest tactics from adversaries.
The Bottom Line on Managed SOAR
The managed SOAR platform benefit isn’t a single feature. It’s the cumulative effect of automation, orchestration, and centralized management. It’s about giving your security team their time back. It’s about replacing chaotic reactivity with calm, measured response.
In a world where threats change every day, skilled analysts are vital. This is not a luxury. It’s a strategic necessity for any organization serious about its cybersecurity [2].
The market growth, projected to reach $3.5 billion by 2032, signals that this shift is underway. The question is no longer if you should automate, but how quickly you can start. The right managed SOAR platform doesn’t just make your team faster.
It makes them smarter, more focused, and more effective. It’s the base for a modern security operation that can keep up with today’s threats.
Start by identifying your most repetitive, time-consuming tasks. These are your top candidates for automation. They’re your first step toward a calmer, more controlled SOC.
FAQ
What real SOAR automation benefits can a team expect day to day?
A managed SOAR setup offers automation benefits. It helps teams reduce alert noise and make faster decisions.
It uses security workflow automation and data enrichment SOAR. Also, it manages security alerts to keep tasks simple.
This helps with false positive reduction, threat detection enhancement, and SOC efficiency improvement. Users get clearer steps, faster work, and fewer mistakes.
How does a security orchestration platform improve incident response?
A security orchestration platform helps automate incident response. It connects tools for quick threat responses and smooth SOC workflows.
It helps with MTTR reduction, rapid threat mitigation, and automated remediation workflows. With event response orchestration and automated incident documentation, teams handle issues faster.
This also improves analyst productivity boost and gives everyone cleaner, easier security operations.
How do managed SOAR services help analysts stay productive?
Managed SOAR services help cut down alert fatigue. They enrich security alerts, triage incidents, and rank SOC alerts.
They combine threat intelligence, SIEM integration, SOAR, and automated SIEM triage. This helps support the cybersecurity workforce.
This boosts SOC team morale, automates security tasks, and supports data-driven security decisions. Analysts get more time for real work.
How does a platform support better visibility across security operations?
A managed SOAR system boosts threat visibility. It centralizes security operations and integrates security tools. Security alert consolidation, event correlation, and threat actor correlation help teams spot patterns quickly.
With continuous security monitoring and threat pattern recognition, users spot risks earlier. SOAR dashboard analytics help them take action with greater confidence.
How does automation support long-term SOC operational efficiency?
Automation boosts long-term SOC efficiency by reducing attack surfaces, managing vulnerabilities, and streamlining security incident reports.
Tools like adaptive security automation, incident response playbooks, and custom playbooks keep operations running smoothly.
Automated compliance reporting helps teams save on cybersecurity costs. It also allows for scalable security operations. This way, teams can build strong defenses and boost their cyber resilience over time.
Conclusion
A managed SOAR platform transforms the SOC. It turns reactive chaos into a smooth, intelligence-driven operation.
Automating repetitive tasks helps analysts focus on real threats. Quick alerts and managing tools from one hub reduce noise.
The result is faster response, clearer visibility, and a calmer, more efficient team. As threats grow more complex, automation isn’t optional; it’s the foundation of a modern SOC built to stay ahead.
References
- https://www.paloaltonetworks.com/cyberpedia/what-is-soar
- https://www.cyware.com/resources/security-guides/benefits-of-security-orchestration-automation-and-response-soar
Related Articles
- https://msspsecurity.com/what-is-managed-security-service-provider/
- https://msspsecurity.com/outsourced-security-operations-center/
- https://msspsecurity.com/how-does-an-mssp-work/